Digital signatures—All about authenticating email, documents and code-signing
By Vinay Purohit, Sectigo director of product management, devops, mobility and digital signature
No business is safe from the evolving cybersecurity threat landscape.
From companies in industrial operations to manufacturing to retail, enterprise-security teams must continually evaluate their security measures to ensure the greatest level of protection against cyber-criminals are eternally looking for new ways to access company networks. Without the right tools and procedures in place, enterprises risk the financial and reputational damage that accompanies a breach.
Complicating modern-day enterprise security are the business and communication challenges imposed by COVID-19. And while digital communications have long been a cornerstone of how businesses operate, the pandemic has forced a large amount of business operations online, almost overnight, including some traditionally in-person activities like contract or document signing.
As critical business activity increasingly takes place online, hackers can unleash sophisticated attacks to gain access to this new trove of unsecured or easily intercepted digital communications. Socially engineered campaigns, like phishing and spoofing, are on the rise as bad actors look to take advantage of the chaos caused by the pandemic to inject malware, distribute virus payloads, and deploy ransomware.
This rise means that enterprises need to step up their cybersecurity practices to ensure their websites, digital communications, and software transfers are not vulnerable to the host of threats posed by cybercriminals.
This is easier said than done.
To reduce the risks of sensitive data being intercepted, organizations are adopting a wide range of cybersecurity measures. One of the most critical is the use of digital signatures, a market forecasted to reach $14.1 billion in value by 2026—growth largely spurred by the requirements of the pandemic.
What Is a digital signature?
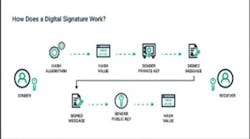
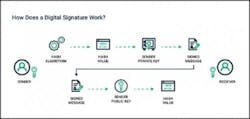
A digital signature is a type of secure electronic seal that leverages public key infrastructure (PKI) to authenticate the identity of the signer. The signature is created by generating a hash, which is encrypted using a sender’s private key. Like a virtual ID card, the signature is then attached to the data, which will confirm to any system that inquires that the data was indeed submitted by the sender.
The signature is uniquely linked to the signer and cannot be recreated or duplicated. Any tampering with the data while it is in transit will be detected, thereby ensuring the integrity of the message. In addition, the system maintains an audit log detailing the signing process. Taken together, these factors mean that an author cannot dispute the data’s authorship or validity, which is particularly important in contract signing.
The three common use cases for digital signatures—code signing, document signing, email signing—each come with their own considerations.
Code signing
Malware attacks increased in frequency last year, hand-in-hand with the rise in working from home. One method hackers use involves code signing certificates to make malware appear legitimate. This is achieved through compromising the victim’s private key and certificate, making it vital for users to sign their code using a highly secure certificate to prevent any malicious activity. When considering code-signing solutions, make sure the product includes these important functions:
* EV code signing for high assurance
* Ability to sign the code on demand
* Timestamping to ensure signature validity after certificate expiration
* Support for both cloud-based and traditional on-premises applications
* Certificate-management workflow
Document signing
Digital signatures are often confused with electronic signatures, which is a broader classification and covers a number of methods of digital authentication, including use of a simple password. In contrast, digital signatures for document signing are based on PKI and are much more secure than other types of electronic signature. When evaluating document-signing solutions, some of the key features and support criteria to look for include:
* Compatibility across document types and integration with relevant workflows
* Trusted by Adobe Approved Trusted List (AATL)
* EU-qualified certificate issuance
* Authentication methods, including AD, OAuth, SAML 2.0
* Key issuance for portable, cloud or on-premises hardware security modules (HSMs)
* Data protection and residency compliance
* Timestamping
Email signing
When seeking a digital-certificate solution for emails, there are several things businesses should consider. Ideally, organizations should use a solution with the following capabilities:
* Private and public email signature digital certificates
* Centralized encryption key storage capabilities
* End-to-end encryption
* Compatibility with multiple devices, email applications and email gateway services
* Regulatory compliance, for example with General Data Protection Regulation (GDPR)
* Full certificate-lifecycle management
* Crypto-agility for supporting new cryptographic technologies
Protecting your organization with digital signatures
It is critical that organizations have the right solutions in place to protect them from every type of digital fraud. Digital signatures are an effective answer to the many threats posed to organizations and their employees by today’s (as well as tomorrow’s) cyber-attacks.
With digital signatures, organizations can trust that their email, documents, and applications are protected by the gold standard in authentication: PKI.